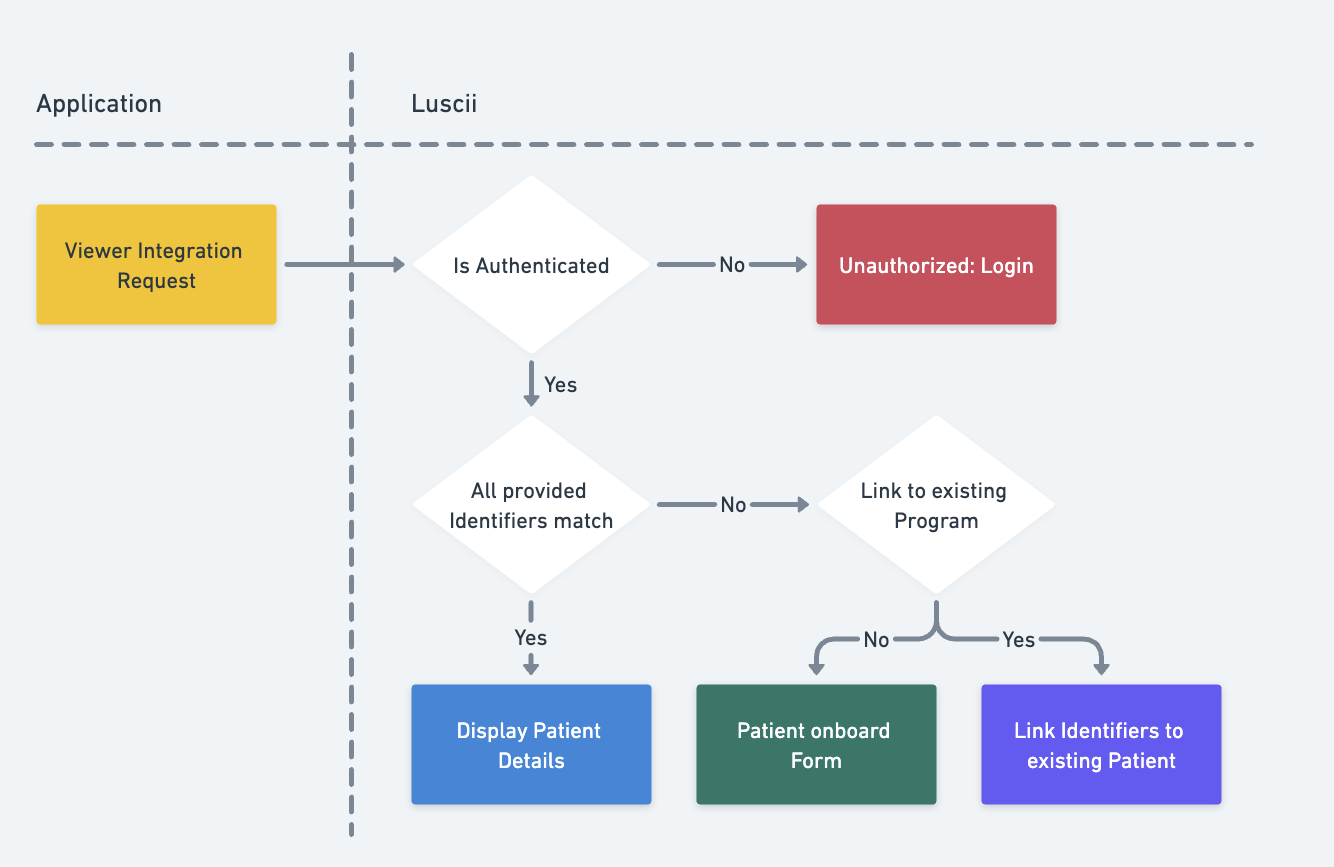
Opening the Viewer
Details about how to launch the viewer
To open the viewer, the iframe or embedded browser performs an HTTP POST request to the viewer endpoint. This can for example be done by sending an invisible, self-submitting HTML form to the browser. The authentication method used is (front-channel) SAML.
Endpoint information
| Item | Value |
|---|---|
| Host | https://vitals.luscii.com (production); https://acc-vitals.luscii.com (acceptance) |
| URL | /login/external/saml |
| Method | POST |
| Content-Type | either application/x-www-form-urlencoded or application/json |
POST body parameters
| Parameter | Type | Description |
|---|---|---|
| identifiers | array | One or more identifiers for the patient (see below for details) |
| SAMLResponse | string | A base64-encoded XML SAML Token (see below for details) |
| patientBsn | string (10) | deprecated - use identifiers instead if you can |
| patientEmail | string (255) | optional |
| patientFirstName | string (50) | optional |
| patientTussenvoegsel | string (20) | optional - infix of patient name, .e.g, van der |
| patientLastName | string (50) | optional |
| patientSex | string (1) | optional - m or f |
| patientDateOfBirth | date | optional - dd-mm-yyyy, e.g. 13-05-2000 for 13th of May 2000 |
| patientGroupId | int | optional - Luscii id of the patient's group |
| patientPhone | string (16) | optional - |
| patientAddressStreet | string (100) | optional - |
| patientAddressNumber | string (10) | optional - |
| patientAddressAnnex | string (10) | optional - |
| patientAddressPostcode | string (10) | optional - |
| patientAddressCity | string (50) | optional - |
| patientAddressCountry | string (2) | optional - ISO-3166-1 two-letter code (e.g. NL or DE) |
| patientProgramId | int | optional - Luscii id of the program |
| patientProtocolUuid | string | optional - Luscii UUID of the protocol |
| patientComments | string | optional - |
The optional fields are used to prefill the patient onboarding flow. The clinician can still enter any missing values by hand. If the user is already known in Luscii, optional fields will be ignored.
Examples
POST /login/external/saml HTTP/1.1
Host: acc-vitals.luscii.com
Content-Type: application/x-www-form-urlencoded
SAMLResponse=PER1bW15IC8%2B&identifiers%5B0%5D%5Bsystem%5D=http%3A%2F%2Ffhir.nl%2Ffhir%2FNamingSystem%2Fbsn&identifiers%5B0%5D%5Bvalue%5D=999999151POST /login/external/saml HTTP/1.1
Host: acc-vitals.luscii.com
Content-Type: application/json
{"SAMLResponse":"PER1bW15IC8+","identifiers":[{"system":"http:\/\/fhir.nl\/fhir\/NamingSystem\/bsn","value":"999999151"}]}Note: In the examples, the SAMLResponse is PER1bW15IC8%2B, which is the URL-encoded version of PER1bW15IC8+, which in turn is the base64-encoded version of <Dummy />. In reality, this will be a much longer value (see examples below), but a dummy is used to keep the example more readable.
An HTML form that would produce these requests could look like this:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Example</title>
</head>
<body>
<form action="https://acc-vitals.luscii.com/login/external/saml" method="post">
<input type="text" name="SAMLResponse" value="PER1bW15IC8+" />
<input type="text" name="identifiers[0][system]" value="http://fhir.nl/fhir/NamingSystem/bsn" />
<input type="text" name="identifiers[0][value]" value="999999151" />
<input type="submit" />
</form>
</body>
</html>Details about identifiers
Follows the FHIR Identifier standard (https://www.hl7.org/fhir/datatypes.html#identifier). Each identifier requires a system and a value parameter. If the value is known within Luscii, the corresponding patient will be loaded. If the value is unknown within Luscii, an onboarding flow will be presented.
Supported systems
Currently the following systems are supported (contact us if you need another one):
| Name | System | Description |
|---|---|---|
| BSN | http://fhir.nl/fhir/NamingSystem/bsn | Dutch social security number |
| Workflow ID | http://sts.zorgplatform.online/ws/claims/2017/07/workflow/workflow-id | Chipsoft Zorgplatform Workflow IDs |
| NHS Number | https://fhir.nhs.uk/Id/nhs-number | NHS number used in the UK |
| Zorg Bij Jou identifier | urn:zorgbijjou | Identifier used by the Zorg Bij Jou system |
Example
{
"identifiers":[
{"system":"http://fhir.nl/fhir/NamingSystem/bsn", "value":"035181011"},
{"system":"http://sts.zorgplatform.online/ws/claims/2017/07/workflow/workflow-id", "value": "47f5a526-163d-4d57-9003-a85b10b2d6da"}]
}
Details about authentication
The Viewer supports Single Sign-On (SSO). Through the provided SAML document, the authentication data is passed, consisting of your Identity Provider (SAML Issuer) and the end-user identifier within that system (SAML Assertion NameId). If this combination is already known at Luscii and linked to an existing Luscii account, the user is automatically logged in. Otherwise, a login screen is shown the first time where the user can login to their Luscii account, after which a link is established for subsequent times. This approach requires a Luscii account to be set up in advance for every user using Luscii through the Viewer.
One way to bypass this mandatory first-time login step is through usage of an API key, which belongs to a single Luscii user and can be generated through Luscii's web interface or public API. If the API Key is passed inside the SAML document's AttributeStatement (see example below), the Viewer uses the Luscii account associated with the API Key.
Please be aware that the API Key is sensitive information as it can be used to fully authenticate as that user. Since the SAML document passes through the browser when opening the Viewer, care must be taken to protect the confidentiality. As such, SAML encryption (through the use of an EncryptedAssertion, not a normal Asserion) should be used. Additional setup is required for this, please refer to the page on initial configuration.
Service accounts
A special use case of the Luscii viewer is to provide access to multiple people without the need for a Luscii account for each person. This is done through a service account, which is set up in advance within a Luscii organization. The service account is very similar to any regular Luscii account and as such you can also generate API keys for it. These are then usable within the SAML document to ensure that the service account is always used. Please note that the Assertion's<NameID> needs to contain the end-user identifier within your Identity Provider system so Luscii can appropriately link actions done through this account to the person responsible for those actions.
Authorization of the service account is done using the same logic as that for regular users. For example, if the service account has the "Healthcare Primary" role, it can see and do anything that a "Healthcare Primary" user can.
Luscii offers a "Read-only Viewer Integration" role especially suitable for providing healthcare professionals within your organization to view a Luscii patient file without the need for a Luscii account. The role can access all patients within the organization, meaning that authorization will need to be done by you before opening the Luscii viewer. This role can only view information, not make any changes, to prevent accidental changes by people with insufficient knowledge of the Luscii product.
Details about SAMLResponse
SAMLResponse is XML SAML token which is base64 encoded. The SAMLResponse needs to adhere to:
- A
<samlp:Response>as root element. - A
<saml:Assertion>or<saml:EncryptedAssertion>as sub element. - When a
<saml:EncryptedAssertion>is submitted, it needs to contain key info with at least<X509IssuerName>. - A
<saml:Issuer>must be present, as we use it to recognize which certificate to check against. - The maximum length of the SAML
<NameID>value (external user id) is 255 characters. - The assertion element must be signed with a valid
<dsig:Signature> - Namespace
samlpmeans:urn:oasis:names:tc:SAML:2.0:protocol. - Namespace
samlmeans:urn:oasis:names:tc:SAML:2.0:assertion. - Namespace
dsigmeans:http://www.w3.org/2000/09/xmldsig#.
Examples
(note that this still needs to be base64 encoded before sending)
<?xml version="1.0"?>
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
ID="_bc588da13f3dfeb28a6726bcda911d67f709b6dd79" Version="2.0"
IssueInstant="2021-06-02T12:05:35Z">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
{{ Issuer }}
</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<ds:SignatureMethod
Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>
<ds:Reference URI="#_bc588da13f3dfeb28a6726bcda911d67f709b6dd79">
<ds:Transforms>
<ds:Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<ds:Transform
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transforms>
<ds:DigestMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<ds:DigestValue>7gyW96pKXd1DgwwRcZB+QHafOoU=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
CPR8Wu//Ms9luIwcwkM+tlKjW7vkiiQSWP6AU73lLB6qWkm9FTN/AVM0bA8+m9AoyJhzg0NZmBX+p/eW9hMsg6q6zv7hmwKWeSszNd4S3zQOLumq3fAsuBFsicYJ0mH3Ss1yc81mExhjZiDIK2y9SeOr5DHQdLeL8H6LNsyj8Rectqb+R4AOp6ZlkNUb7Ri8H5MCcx7V4CqEafWYl3o7DGXxxS8O7vpw7Y7ekEb9MWh3fgw6ij7vQVQS5Bj5Imr6nSZM2jQK0MjYgu8MNLMwjlvvetyNubx285/oqUYn8JjPF8l0fK0XlXhbc/+/FifqpTcP6bozzpsZYUvgVXCLTA==
</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIIDpTCCAo2gAwIBAgIJAJh5SZ9Naj3EMA0GCSqGSIb3DQEBCwUAMGkxCzAJBgNVBAYTAk5MMRYwFAYDVQQIDA1Ob29yZC1Ib2xsYW5kMRIwEAYDVQQHDAlBbXN0ZXJkYW0xFjAUBgNVBAoMDUZvY3VzY3VyYSBFTVIxFjAUBgNVBAMMDUZvY3VzY3VyYSBBU1AwHhcNMTcxMDIzMDgwNjUyWhcNMTgxMDIzMDgwNjUyWjBpMQswCQYDVQQGEwJOTDEWMBQGA1UECAwNTm9vcmQtSG9sbGFuZDESMBAGA1UEBwwJQW1zdGVyZGFtMRYwFAYDVQQKDA1Gb2N1c2N1cmEgRU1SMRYwFAYDVQQDDA1Gb2N1c2N1cmEgQVNQMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAn4nyAdVakRNrtArAeAcRX2RUQe0eCWRZhHFYtd9Xe2REKBNwIGvGbOvaRuFeI1mxmZ3t1GClauVx8BFtbUNoN86ItOs0QtQ2pmf1tuuWmdt9DcQ6FsqzV2NOAkeX+IZuGx2LLl/IvPN7ueMiYATG4pEFbXtGR+mwNl0Okk43kXVnISl/XLV7W9UYiKqKEKMKaUC6Ut9EOMqBA5RBLJZoE1ULrN1IVMxQ03tEtRQVUKMTrM6SWPhuaOc2fMJuXhQt7yiX1PTWdrWH/Ja6Sp0Vk94Bpv+3yfDa7U/K/HCDr+2fyK2gCbOM+pxJOsQx0CUSe2OZje6Ub9CCq48U8bVikwIDAQABo1AwTjAdBgNVHQ4EFgQUVBFvt6uoijuKlvo1WtxitMGUzkwwHwYDVR0jBBgwFoAUVBFvt6uoijuKlvo1WtxitMGUzkwwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEASgHsiyzuqi6eGxze+kCVLUjvRwONpe4au3TsXlc3g2ESJZLhdK6BbH4xfd2bfhJJT1oDi7hdpsuqZeHBskfmXTO9S5Yv7R4T73av8S21c9d70iJ126AkFaY01XpwHA2gRAcGSZlkw9AhrReW9hHwdU/X1XRYY+7xqlSbp94RsgiJyW06SuxcDqTtS5Y44rjGrYFObgo9XIF2XnJYXsrv1EaHX77urSdwa+Gl+KJIc0N+FJUiGp29ykM60dgY9W3go1z1L+m3sCdXxIbo8jepSz0DZXbAx5lhDkOAIPCkYzpOvYpuA4e8hm76/kHtPJvwJMB1N3A4gT0bgaYvhD0npw==
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion"
ID="_b726f610a6fba37a537b155a52f775f41a52e59f5e" Version="2.0"
IssueInstant="2021-06-02T12:05:35Z">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
{{ Issuer }}
</saml:Issuer>
<Subject>
<NameID NameQualifier="{{ Your company name }}">{{ Your user id }}</NameID>
<SubjectConfirmation Method="TestMethod">
<SubjectConfirmationData NotBefore="2021-06-02T12:05:35Z"
NotOnOrAfter="2021-06-02T12:10:35Z"/>
</SubjectConfirmation>
</Subject>
<Conditions>
<OneTimeUse/>
</Conditions>
<AttributeStatement>
<Attribute Name="ApiKey">
<AttributeValue>{{ API key of the Luscii service account. This attribute is optional. }}</AttributeValue>
</Attribute>
</AttributeStatement>
<AuthnStatement AuthnInstant="2021-06-02T12:05:35Z"
SessionNotOnOrAfter="2021-06-02T12:10:35Z"
SessionIndex="_bc588da13f3dfeb28a6726bcda911d67f709b6dd79">
<AuthnContext>
<AuthnContextClassRef>
urn:oasis:names:tc:SAML:2.0:ac:classes:Password
</AuthnContextClassRef>
</AuthnContext>
</AuthnStatement>
</Assertion>
</samlp:Response><?xml version="1.0"?>
<saml:EncryptedAssertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
<xenc:EncryptedData xmlns:xenc="http://www.w3.org/2001/04/xmlenc#"
xmlns:dsig="http://www.w3.org/2000/09/xmldsig#"
Type="http://www.w3.org/2001/04/xmlenc#Element">
<xenc:EncryptionMethod
Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<xenc:EncryptedKey>
<xenc:EncryptionMethod
Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<xenc:CipherData>
<xenc:CipherValue>
kd+Pd90ItCU0jnnvuabADBB7KdbWxt7bufIvoYBqhljMwqS5JrFtl7FOECfa+wdMIQ3lRmqiw+ZM0E7wrSatIaRjxHYq90PTmIwRx2phFtlO33Hmq3fCr23JzEhvvXszeaVj8tkfVHXgs45Ze9ae4xhNhZ+PJ87is3ylRZp12oQ9F6LGUG4a2l670xiHaMO7tN3J5hMLovmqTaj6fa9U5ef+6BEDAJDEXEnVkOcKpL6GASef1HH2N3Xi4NnhLoYy2DybskSuMZdvU31L5ZaGD93CFPR7E7WPiIeYaDC/Wmg7SWl2WNfPxLLHYQzAE1RTqsGJIAWP7V2NXAt01w6rFg==
</xenc:CipherValue>
</xenc:CipherData>
</xenc:EncryptedKey>
<dsig:X509Data>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>{{ Certificate Issuer }}</dsig:X509IssuerName>
<dsig:X509SerialNumber>{{ Certificate Serial Number }}</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509Certificate>
MIIDzDCCArQCCQClCLUeC8zVGTANBgkqhkiG9w0BAQsFADCBpzELMAkGA1UEBhMCTkwxFjAUBgNVBAgMDU5vb3JkLUhvbGxhbmQxEjAQBgNVBAcMCUFtc3RlcmRhbTESMBAGA1UECgwJRm9jdXNDdXJhMRQwEgYDVQQLDAtEZXZlbG9wbWVudDEfMB0GA1UEAwwWRkMgRU1SIEVuY3J5cHRpb24gVGVzdDEhMB8GCSqGSIb3DQEJARYSdGhpanNAZm9jdXNjdXJhLm5sMB4XDTE3MDkwNzA4NDcxMloXDTI3MDkwNTA4NDcxMlowgacxCzAJBgNVBAYTAk5MMRYwFAYDVQQIDA1Ob29yZC1Ib2xsYW5kMRIwEAYDVQQHDAlBbXN0ZXJkYW0xEjAQBgNVBAoMCUZvY3VzQ3VyYTEUMBIGA1UECwwLRGV2ZWxvcG1lbnQxHzAdBgNVBAMMFkZDIEVNUiBFbmNyeXB0aW9uIFRlc3QxITAfBgkqhkiG9w0BCQEWEnRoaWpzQGZvY3VzY3VyYS5ubDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMdIn4l98iTL3/E8vcmAejJZIx30MmcVO71TnQA2G4Nnhsangu9efeW9ZKRPQwb3nsULTw7jfJEjPSkOtViQPxF97c/X+hOaD+aT1F8H90dAKHdje2rmREy9Ekv7LWCsMt1C22QkIxIxl7xXiyVDfy8KDktXz5GXaBPBcCLJQJaJX46o8sJLO+8fw5dvYdw+f//o8NlyXP0z+37bQsJu2vL/Ecvoe3ZbHNVkUhkR29PC+nMWc6mkiFTWs9yuU93eI0iKaSJ6pYWStgmWL+jJbcBI0b4vuMej+148ZC/QqBscPsTADTIPTM4G+xSBGlaTuOmJWSGU9AiTiNaofHvGyvECAwEAATANBgkqhkiG9w0BAQsFAAOCAQEAw3DntqYbHs13g7kihGzbBLoq48ZJBeFbGO+mWq61EBs7yQO8cPrEXQUGpO2Dg8qYvs8BjxNs3/0AjJIQor3Ry5FAUu+rN5hh+0G4EXKG+OcFsgmnIqxFXylED27cGCTSuo5ysuOu1jr0G6wTnUOl8utEB/tDkL9vz6JvL0qDaK603hy1vGvpsMUrzyQr74776g2KfuflY1zGamlZKJkeB3nGdOt11eY8tt5e1zqhxCVzcANT5GbW65lPTn4hwmo6MDuuMtv2uB6G2DoO+XU4qUAe2KH5fBtkGqOOvqVUjMZ+hnQ8t6LERY2RTuQxNQS5h/LneZTq+iMizIZMGhcd6w==
</dsig:X509Certificate>
</dsig:X509Data>
</dsig:KeyInfo>
<xenc:CipherData>
<xenc:CipherValue>
mZI4WJqOHP/w1mw0sOICq0fpfDzpXv81bUkc7uvFiCs9QTnTdeIGdBVVL4CncX0kkuJhvYm+IVtOBXZe3UyrPuCBcoA4wnlUzBZhy4lwAn8IqX5bwKw6YH6gP0JLgKHH2yAkhvUlW/FyGKOWyZFJIMEJFK4ntJ3Er7J+kEhd4ktS+JXKT1cKGlCrsLN5RYneskzrm5zifKZPmjpY1Y1lTwWJK6oIQsv0lQa4AVmrmgfkPB76d7kG5olzBcAPfj5nnikIhU58I+UcJQCOGqdPwyXn5iYiQRJJ4NsYXucXNe/lrWyhMdrJm6aTwOG09TZl8Dgur0Wnqa20Z6vntG3VYbA55jzoC4XMX9ad96v21/ilLnAfHm87TJ9fFauJMyVqzR6d22p2B2hNN9annaPHx77DWj5YAYkfTi67/m+nytR5QllbutS9kzv+GBQiigP8d9daNP8LS1uRcGLVA9BD5pWi8DutY7uTWF4fw1QX4VmwkWuNJQ3fKdvzXiw5Kv4GSgeccVYggxAa4l+2oPVfz9s4+KHfIpyz5B1aNMiCwhJzwsSxR8CWNo/fkH/qY9xNMlWH9H7HUM5UDlhxmp323B23cKWQzFBRq811fMcGBgZlBnOBOwNujdCpNO3mjkKcimNs6ajmx+4mncj9hWKqdvrG/ebZKN1oSzzE3R8HAxjphJxbrWGrmZRtncIP3YcZLBC8tX77FtDYoFevNgtSquOxj+M8Y8hFVWF1lTUWUxq2IgNcXb32W+kJ7FwusBxfFIrad4TIv7EgBvLBox+m5xNMJOv2SUjfOUjNnfhWpFPzeYFzsqfE1hE9f27ImK0QHmMCIuWpMsM1VXYP440yIZvKdHOfSNq0TMc9yvtByk2b9HXS4nj2RsaFLH2JCJjOFNT1CjgscxlE9Eq5z/pf6Gb2HuvQ28H+4qP+aqOSS2G4ODeohTqEi8M5VxadJXd++YUPy/C1m/hh55/W6gyIRDYJdnbqQVrCR58xxZbnsxyLsxE8WCD2FG2SDCyZ3lpdaMNCYY776HQ2Gts6wPBaBvjqa34K7Mcb1Ano1UXTNxiM7GWz+w5JZXehqeUGAasa7t5nnnuTuG1N8ClSgx+AI33HC/k7STxlMvjiKU9vJHahsntp4XD3tis/syeQbIbGFTJXhNL4ETJQPqsrjGe4vOdp7YH0W0RjWCGq0/T/mFnFnmKR2GJRCR7tMtsKIbORfAdpSTfSpSfPJGKwhvQiVDBZNithD7pLme3MiF/FOQx7vsLmX1+bxGWEsPTp+1a5KqN6GyZEWroOLTptcndQgtdOqa41cWXUBQi4WOqsUwTLEhPMSa6PdnfXdMy8XqXR88NKeIMNwBDRNQ2mpxTO5jNaLKxArhjRHfxaxdgNA40mKbwU++MtEw43xqPeA8s/N6wjEs1/pCb6g6W/vHbiDXa27s4vku6VtN3SC2P30nezPb84BcFEhuHur8gsN4yT35J9VY5k2GUGzKPpqJvqUPsc0IdPon6yWKWMJJQc269kPXI8yZ9PX8T1IIkGJFR3ssuJbx44VjZkd2S8oAxyPMpm1Q0mhdQlUZYUS/2lPsGbIva4CazYqY6+6Jpy3U2hgCP6PajJUR7TdkelFrpXjBra7km5dgUaUW9hrzA4bSBy4/CQybBxUtzqaPUaOeWLkmxNj1cjj3k9Hb1mNJQzxNqSXIpNioNtPp7tghDBIU7EuUo/PTzyrd8N3VYmZzI2HisDd4ZsG98WWtL/8RMppuwvnhcRwDGAp0ZgmFiW05fsmPyxhoWxJnGXpG/YndPWCRaOFaoOivGaiFdoOmbCtS63tmWR8qAOHnOiI/9bETcnFy/SV5Ark6eogtq+u4UJbs60Ny822qb/kiy7sL1BGFIeJd1I0GoOvyQggf1Cb/PRV+HnU4SV09iyWi1Mp2+ZN8QJ8+aGTvKpCYTJ4aiG4EBAEMiD81ovUIVccH6LQN1hXUPlTRVwhn1e/MhjAIk0zTmtWna4nE+SWhcMwwmHHDmZ0RjVen+CKRMmb2HW9TncZRcyncM/2SjnGkDs/kZks7NvsyU//9GmCuwOAmNNBqcwIOp66DczJj2Sv11O+D9NqPV2f+oHzSGh+TKRc9lKSCz9STBEct0q/aLe4anQ/TlnV8xjbOrBqtznVKYG5otW3HM18B2nWQJsNDvCo6uEAa1Kv1lkS6UL1S0Y19/6oZKWkytaHsf0KMdvqh6W5SNkYy7b0Sj3UdZB9Nq9kPEBUHratTHDtfLbYZ5Np0hci9zfcW+TiVgqni2PDUdFHI1yLRodthxPkaksHIoHu8I7r81cUQVa6+vC3HBrtXYLoOmerzY6nSKrNaURg7Nl6aWcuEEB9/eKSzFRf7G0WSZ76rHE7maWt3/2V9nW+7RI9NVGyOWOsfWe9J32t6r5cA8Nx7ZgoG49oE8TQzra7uoicvARhY/+ds/J3S1qxRMap3ZSWh7Sr8lxIJCnnqwo/k3Lfv864Z0tyAiKiOkvbjURuwnPA08Kdq3GcP/+iIGD+G8MQKddqXsin1DB6A+kI92z1pXcCX+pEy6lPGYv/XxMMw9Px6/7zFeZypjAp5XmP9PF8nmAh5RLpAG3LbbsN6dUN9XmkiH0FVG4TcGqb9pGitJXUyMAs/cP9qWpugIKYDxACdMGPuQG81gsZn8hgh9xp9g/hAcO4oi12Yq34wMa9jIQf3c4OgqRPB1W3fKZyhFmiJvgU+McQBslvZeEG9p8hnZM3+vYDqOJsC20hO3TcHDZze6Uc0B4T8xnOA0VHxj4uPPW5o5cBtpRFcou0ZJZ3GeCvrQPrJWOHSwuKb+HrOlDQHY+OgONGxY5Whj+MDDn3m/UunLhTbLToVB8ADj0wy11Hg3uuBI3BTnyXyG4FoDtYCK+YYuHE1qaUbOSsiDQsmMLZ10bGnwqQvi+AROwkCvdQHKirm5yci414N8J6nZiN73H6woLCWp06M8ILCbQ4lcR88CEON0ry4FoBHa7iQcDYICLzQXckOrsFiXbJjrUWfJ+xrd5K9jNNMS+KOwKnJVyHRIgWUvoyr80qtZPiQ5mp/6fagks71iGBwch6EIGTP7cOcSGWb7G521wzvj9mJHelH56Gnl9qT0WWcr4R4g5fs9+cVOq9D4BYX/wQOeT1PfJZwqV67YXeOtt0XCT5OFcwP1c38hZIM009rzHQl79XxR3RMDWizc/3fFsk3FvjgzAFAocVSduws3YCfD4cVp91dXG8ubMXDR3D5wtTMW5py++wWg7Midl9YmjHJATEsTxgkhgEwydl8boo/4lhTGm10a7lf1SF1n2fO2/R6x6fABQZGspRrrQQ0LAUjTliNHMvjVcl7FTMFA3JB1Krnn8Zn+uP5EZB/6nmNjWK0Xk8RFziL9u/yPkNF6ANfUadNjj41SzrwIIV8SSXL39kbtY9eT3FHj2LWy3uClXtXgkMwoC8CmVynx0uftZo15kjOBzCJhn3ivGh3OdfPFua4ypgIBvBZv1rAkyO9QGtWWzmHvK+8ZiDxjzD9N+J3HVWzST7Txj/F3P6yrXCKSRTaA7L0dO+TifR4szxBE3uatEhRr2NGQYuaOTr8yKrD16UM6ZyOCJDBH1QHOyEM5nbEn29NJdR4ZBFUR8HFZgS0yuc2KntoMgt89eN12dK5rkTa6q77lt+EkJhdGUqCqJ/b47qOsdOR9+TfJb7RZloYB2Ef6HhiiWS2totWVahW1Svws52971oxP+uXs1CHq03+3a7i8vP3RvLL91ThhuWptRXyYUo+DwtkRl0BcjqBHcC/J+QfLcAMD3GIIQCTJY2APVeRIzRIjtOJZX3Hlp/KYJcUilN44sK7VwD9DS8lXZ4wp/CtVMmlqgM8YCA0qwAICMVFBhgK7pq3/Vus4elR316HFNayCWN0jUd0mCbJM65kc0gjISvet/xPV0zpT7iVxYIxDEdeG/7IOahLOSbbucfUiXDqO+NxU6/KNC2pxZqL3/8XGoOPwJuxnNmUxPBi9Xwz3wJUYYCPfHZjiCxNZE5HibUt+b0NjxG8BEAtpYHwLpMIyFaSquNh4vc29U6vXtxfB7/NIbcK2IRilgJrQ0VwNM62sdtVI3RE31ilSnXBP1qoviqTHOeaEtaR2so0mkuhQoObv+8T66x83Q6l8V6F0h3OtDi0kHs3XvYctduhXAcUo75lmmmdUUopB9pqzAFK64rTjAffX5VPmX+tRGmUQgwqkSjTgWK+6yJ9Ew+02YYZtxEj3W414DL0v1+YiyQZHSXkMIF13oveqEGF/5YPqCRP8dopMWxtY/YbxZJ3bh1J/VoYmh9qF70i2dHXUcqBlrfLKw0xrdSUSPaesaRnCVWFKAdvYFfB3QWm7XUmbGXERocL5DaZN+OHK3+DBVZKMbyp8pjCzrHkmr5+DOI39YUtYBCrbeSxaCIpuuM831Dt1pkWQ4YQ4queaeve9Or6Ed4mOUc7qg9XpFHPpqZiUYsI81GGJh3hnFrYDjOSsH0aVExGFjP/BTH8U5XbI5OzDEgtZ78qm3s3apinQsytZeIDl+ngXnkNSYsG5joPZor8AqfZ/lvdBpRjQ4GcGU8ts4JoNH6F2Qm5WwYUpfjM8j2o27RwzpsxKGH5wCKFRGs9xDyWji3HwXL1lQUadrhJHICUO5SSDMPIOls0YQKqFxi5zyZHWEH48j4cvv2cFMzdxmb3XhWGnKZY8ua34byo1d05WESNcQVpOqc4gPHBNEGoaSsnsZqV5u4wiF+d6yu1FTTXdt59pcEa6MJVbP95+OwXF7dtrhKmtW5uIdTWf1eNK+XPeSDKAxp13SwAS6orQvwy/2L24wC1gkK5nJbmMz/Fi9/lYjlwIJj4AOXkNSkcaLZXYjYCfG+nGvBbr3Clf4DfXSnEEKkwhx+MpzmaH6/C15nA4pUCEWHLauQDhNq6JpSHGX6sOug4NBXTwiRGvrlU6rHjV8PoUiIsjZ0ZIyJ1CfrQw5h2yPhEP7r1gDaw3t1wGd9hUALeZwpMDYtV9aNwe2T3pR3dUzrZbEiRSke51d9PXJP5lge5bNkyIgLK/zndCfezDS2JfsHGUzHqFvwxQ4mf7YTu+Nb9rL8xDcX8Y2KgB0Kn7wfC/gTzepx+aL7DHj2ib8
</xenc:CipherValue>
</xenc:CipherData>
</xenc:EncryptedData>
</saml:EncryptedAssertion>Updated 3 months ago